Welcome to post #2 of 3, publishing the results of three dialogue sessions between Richard Kaufmann, CISO of Amedisys, and me. The timing of our conversations, tracking both Richard’s and the company’s evolving approach to cybersecurity in health care, has coincided with the Change Healthcare breach and ransom that emerged in February 2024. This second blog of the three is being edited just days after Andrew Witty’s testimony to the U.S. Senate Finance Committee which convened a hearing on May 1st themed, “Hacking America’s Health Care: Assessing the Change Healthcare Cyber Attack and What’s Next.”
UnitedHealth Group acquired Change Healthcare in 2022, and so Witty, UHG’s CEO, was summoned to speak about the breach over an intense two-hour session which both Democrats and Republicans grilled the executive of the largest health insurance company in the U.S. based on revenue (with Kaiser boasting more insured members).
The Change Healthcare breach could be, “a case study in crisis mismanagement for decades to come,” according to Rep. Cathy McMorris Rodgers (R-Wash.), chair of the House Energy and Commerce Committee, who was one of many interrogators who met with the UHG exec.
In another timing-is-uncanny event, on May 1st, Verizon published its 17th annual 2024 Data Breach Investigations Report noting “new and innovative attacks” deployed on top of the “tried-and-true” tactics that have been successfully used by hackers and bad actors in the previous 16 years.
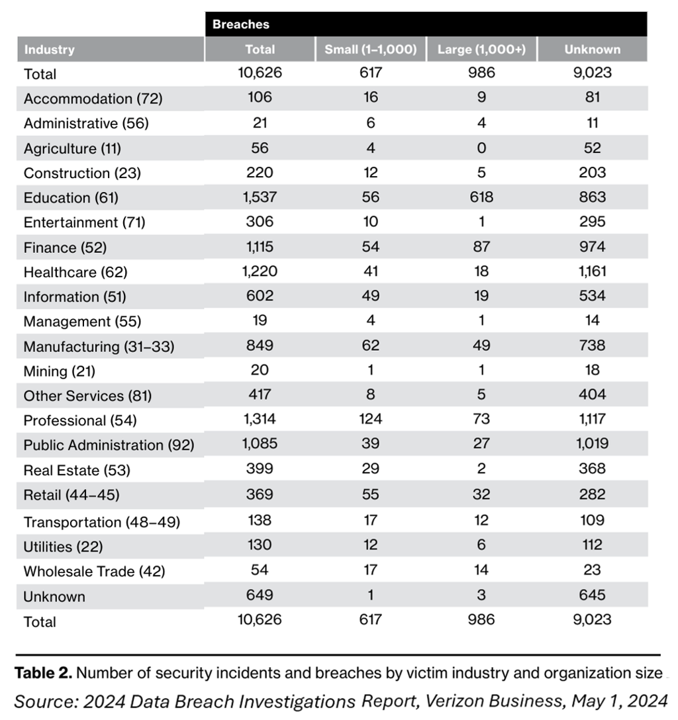
This chart summarizes Verizon’s findings for the 2024 report, calling out healthcare breaches among the most frequently seen last year – just behind breaches in the industries of education and professional services.
In this detailed and engagingly-written report, Verizon profiles each of these industries in some detail characterizing the frequency of incidents, the key patterns, threat actors, motives, and types of data compromised
Here is Verizon’s take on the Healthcare industry, finding that personal data eclipsed medical data as the preferred target for the threat actors. As Verizon puts it in the report, “medical data doesn’t even get a passing nod,” calling out personal data as the flavor of the year because, as the authors characterized it, the threat actors “don’t really care about Aunt Bertha’s bunions.”

With these contextual events in mind, I kicked off questions with Richard starting with Aunt Bertha’s bunions – that is, Amedisys’s view on the mix of data assets to protect in the Amedisys ecosystem noting Verizon’s “Attributes” shown in the table.
Jane: Richard, as you and your info security team embarked on re-imagining and planning your renewed approach to cybersecurity, do you prioritize data assets by type? Are there different technology solutions you considered to deal with different kinds of data, say financial versus clinical versus demographic?
Richard: At Amedisys, as our security strategy developed, we always knew that we wanted a data centric approach to protection. Data protection, to your point above, is an extremely complicated and I would argue, almost a unique problem for every organization. When we think about security at Amedisys, we approach it from a few different angles – Identity, Endpoint, and finally Data.
I think some of the things we got right in our journey was first understanding how our organization provides care. As we discussed in our first conversation in this series, Amedisys treats over four hundred thousand patients each year, many of them in their home. So, the first thing we did when securing our caregiver experience was to focus on identities. That’s where we made multifactor authentication (MFA) a requirement for all system access and simplified the password process for our clinicians. After identity, we evaluated the technology platforms our clinicians leverage to treat our patients and we hardened those systems. We had some great help from Microsoft during those projects and they really accelerated our identity and endpoint program so that we could focus our attention on securing our data–which is a big undertaking.
When it comes to data protection, this is an area where I really wish I had a second shot to do it again from the beginning. The primary driver for that feeling is that data protection technology has matured at an incredible rate over the past 5 years. To me, the best data governance solutions were always made up of equal parts machine learning and human confirmation. With the advancement in machine learning, AI, and data loss prevention (DLP) technology, I would love to go back to the beginning and challenge my assumptions in this space.
The biggest lesson learned for us was we didn’t focus enough on Exact Data Matching. We relied too heavily on the machine learning aspect of our classification strategy. That’s resulted in lower fidelity signal downstream. So, if you’re a security leader out there and are thinking about modernizing your data governance strategy, start with an exercise in Exact Data Matching, it will save you months of rework down the road.
Jane: A recent analysis of health care info security asserted that, “There is no patient safety without cybersecurity.” What is your take on this with respect to Amedisys’s patient population and home care operations?
Richard: I would revise that statement slightly, but it’s an important distinction- “There is no patient safety without privacy.”
The line between privacy and security should be a beautiful shade of gray. In my opinion, security enables privacy. At Amedisys, we are incredibly fortunate to have an amazing Chief Privacy Officer, John Cowley – he’s one of the sharpest privacy practitioners I’ve ever met. The collaboration that takes place between privacy and security is critical to both teams’ success and I don’t think I could do my job as CISO without the support and clear expectations that John gives me.
We are learning that expectations surrounding privacy are changing. When I first started my career, and before things like social media, many people prioritized privacy. In 2024 we have content creators who are doctors. Patients obviously want their data to remain private, but they also want to have a say in who they share it with.
I think that’s one of the biggest challenges healthcare is going to face in these early days of AI. How do we keep the individual’s information private, while leveraging that signal for the greater good? Clinical decision support is a great use case for AI, but patient safety and their right to privacy is a delicate line to walk.
Jane: Looking within the organization at Amedisys, I think about Verizon’s observation on the evolving landscape that a CISO must navigate – in their words, “balancing the need to address vulnerabilities quicker than ever before while investing in the continued employee education as it relates to ransomware and cybersecurity hygiene.” In deploying your strategy, how did you deal with the real-time environment of breach risk management and the need to continually update and educate staff? Then thinking about the staff and that education and updating, is cybersecurity “everyone’s” business in that you have ongoing education of both your direct team in info security and the larger organization of clinician folks as well as administrative staff?
Richard: The typical avenues that most security leaders go down for employee training has always seemed flawed to me. I’ve mentioned it before, but at Amedisys we are all caregivers. Delivering a culture of security is just an extension of providing that care. When we talk about employee security training, the de facto answer is typically some sort of phishing assessment. I really despise that premise. If your goal as a CISO is to drive a culture of partnership and collaboration so that more employees understand what the goal of security is – why would you start that conversation by tricking users into clicking a link and then taking training. It’s 2024 – everyone knows not to click on the link. No one has started a job and on the first day walked into an organization and said, “I can’t wait to click all of these links.” My 7-year-old, who doesn’t have a computer yet, knows not to click on the links.
What a different approach to a cyber aware culture looked like for us was leveraging the information about real campaigns impacting our organization. We coached our users and helped them understand what their own threat landscape looked like. If security teams can step back and analyze the types of adversary activity specific to an organization, there is a good chance you’ll start to see patterns. Adversaries target payroll, HR, and caregiver populations differently – so if you’re really interested in driving a culture of security, you need to show up and coach each of those teams with that context.
I do think everyone in an organization has a role to play in keeping that organization secure. I also know that if a nurse showed up at my desk and told me I need to successfully put an IV in someone’s arm, I’m just going to skip to the computer-based training. My expectations have limitations and when that gap starts between expectations and reality, that’s when we deploy our training.

Jane: In Andrew Witty’s testimony to the Senate Committee, at times he blamed “outdated technology” for the breach. How do you deal with the ever-changing technologies available to you and how you plan and implement a strategy – needing to account for evolving technologies and applications? How do you manage that ever-changing risk environment vis-à-vis the technology, processes and people?
Richard: One of my favorite cybersecurity podcasts is Darknet Diaries hosted by Jack Rhysider. In one of his episodes, he reminds us that we are still in the literal infancy of the internet. Development cycles are only getting faster and with AI out on the horizon things aren’t slowing down. So how do I stay on top of an ever-changing ecosystem of tools and technology? Outside of great podcasts like the one above, The Beatles said it best – “I get by with a little help from my friends.”
Since becoming a CISO I’ve been able to meet other leaders that are really doing some amazing things within security and healthcare. That tribal knowledge is something special. The group chat and Teams channels I’m on with other CISOs are incredibly helpful. These CISO communities offer perspective on the latest events, which vendors are the best to work with, and sometimes just a great place to rant when it feels like no one else is listening to us. Which can be often unfortunately. I’ve developed some great friendships from other CISOs in the field and I’m forever grateful of all the help that those communities offer.
At Amedisys we leverage the full E5 suite of security tools from Microsoft. Talk about a platform that changes rapidly. We’ve been able to leverage some amazing expertise from within the walls of Microsoft as we started implementing that platform. I’ll be the first to admit that sometimes it takes a few tries to get to the right person, but once you do, I’ve found the help that Microsoft provides incredible value. I’ve run into a few security leaders who tell me that “Microsoft isn’t a security company”, and my rebuttal to that is to talk the security engineers that I’ve talked to. There are teams there that are designed to help you move whichever needle needs a nudge.
Another area where I see the impact of the speed of change is in the C-Suite. Security is bespoke, and as such, it makes sense for the CISO role to start moving into the CEO reporting structure for some organizations. Organizational leaders are starting to shorten the reporting structure and value the insight that CISOs can bring to risk-based decision making.
JSK post-script to post #2
In this second conversation, Richard has shared many milestones, learnings, and pivots in Amedisys’s cybersecurity journey. My personal lightbulb moment in the wisdom in this second round of our discussion was Richard’s over-arching question: “How do we keep the individual’s information private, while leveraging that signal for the greater good?” This will be a key pillar to building trust between patients and the health system ongoing.
In our third and final conversation in this series to be published in late June, Richard and I will brainstorm the future of cybersecurity in health care– considerations, scenarios, and wild cards to keep in mind as we continually plan to bolster information security (and trust) across the health care ecosystem. Stay tuned!




 Interviewed live on BNN Bloomberg (Canada) on the market for GLP-1 drugs for weight loss and their impact on both the health care system and consumer goods and services -- notably, food, nutrition, retail health, gyms, and other sectors.
Interviewed live on BNN Bloomberg (Canada) on the market for GLP-1 drugs for weight loss and their impact on both the health care system and consumer goods and services -- notably, food, nutrition, retail health, gyms, and other sectors. Thank you, Feedspot, for
Thank you, Feedspot, for  As you may know, I have been splitting work- and living-time between the U.S. and the E.U., most recently living in and working from Brussels. In the month of September 2024, I'll be splitting time between London and other parts of the U.K., and Italy where I'll be working with clients on consumer health, self-care and home care focused on food-as-medicine, digital health, business and scenario planning for the future...
As you may know, I have been splitting work- and living-time between the U.S. and the E.U., most recently living in and working from Brussels. In the month of September 2024, I'll be splitting time between London and other parts of the U.K., and Italy where I'll be working with clients on consumer health, self-care and home care focused on food-as-medicine, digital health, business and scenario planning for the future...