We have entered an era of insecurity in healthcare in America. While major attention is being paid to healthcare insurance and service insecurity, food insecurity and financial insecurity, there’s another one to add to this list: medical device security.
As more medical devices have moved into the digital internet-connected mode, the risk for malware, ransomware, and overall hack-ability grows. This increasing and challenging risk is covered in the report, Medical Device Security: An Industry Under Attack and Unprepared to Defend from Ponemon Institute.
Ponemon Institute has been tracking information security across industries, including healthcare, for several years. In this survey, sponsored by Synopsys, Ponemon focuses in on healthcare polling managers who work in medical device manufacturers and healthcare delivery organizations (HDOs in this report). Surveying these two groups provides insights into their alignment on the issue of medical device security. Importantly, it’s a lack of alignment and, of concern, cohesive strategy, that’s discovered.
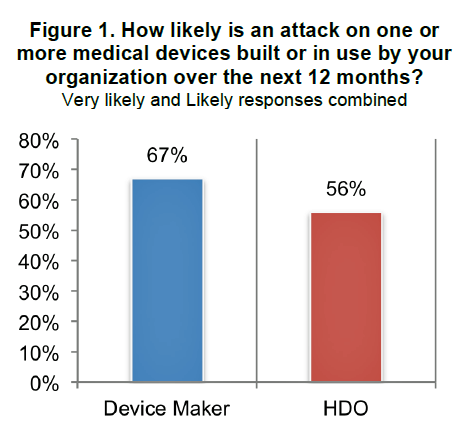
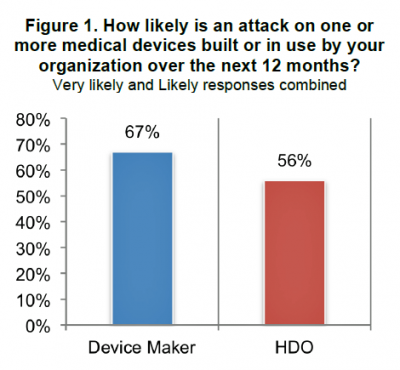
The first chart clearly shows that most people working in device makers and HDOs expect an attack on at least one medical device in the next 12 months. But only 17% of device makers, and 15% of HDOs say they’re taking “significant steps” to prevent an attack.
 This is a weak response when 40% of healthcare providers say they — and their patients — have had a security incident with a medical device, and 31% of device makers are aware of such incidents.
This is a weak response when 40% of healthcare providers say they — and their patients — have had a security incident with a medical device, and 31% of device makers are aware of such incidents.
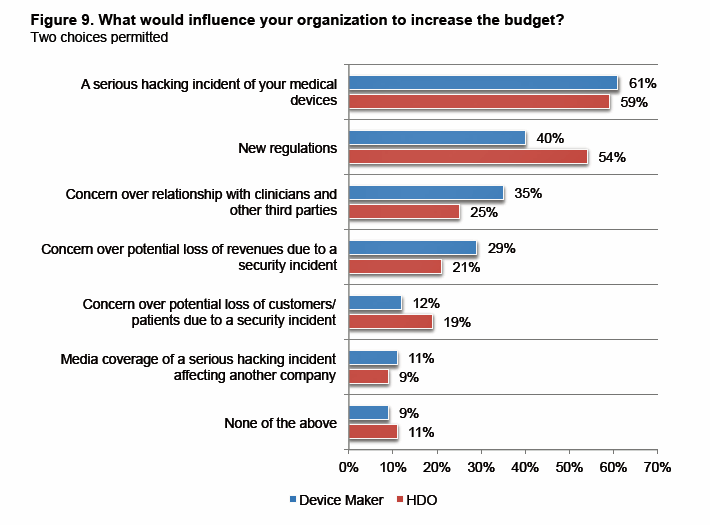
What would motivate these organizations to spend more resources for securing medical devices? The second chart answers that question: a serious hacking incident first would influence both makers and providers to allocate more resources for med device security. A second driver would be regulations, especially motivational to healthcare providers. (THINK: HIPAA and HITECH incentives for EHR adoption, for example).
In the meantime, until such a major hacking incident might happen, it appears that med device makers and healthcare organizations are largely muddling through the security challenge without holistic prevention and mitigation strategies. More healthcare providers sound confident in their ability to detect security vulnerabilities than are the makers of these devices; and, fewer (25%) of makers are confident in security protocols and architectures that are baked into the devices to protect patients than are healthcare providers (38%).
A main contributor to med device security risks is vulnerable code within the device. The reasons devices contain vulnerable code, the survey respondents believe, is a lack of quality assurance and testing procedures, a rush to release the product which pressures the product teams, accidental coding errors, among other egregious practices and policies.
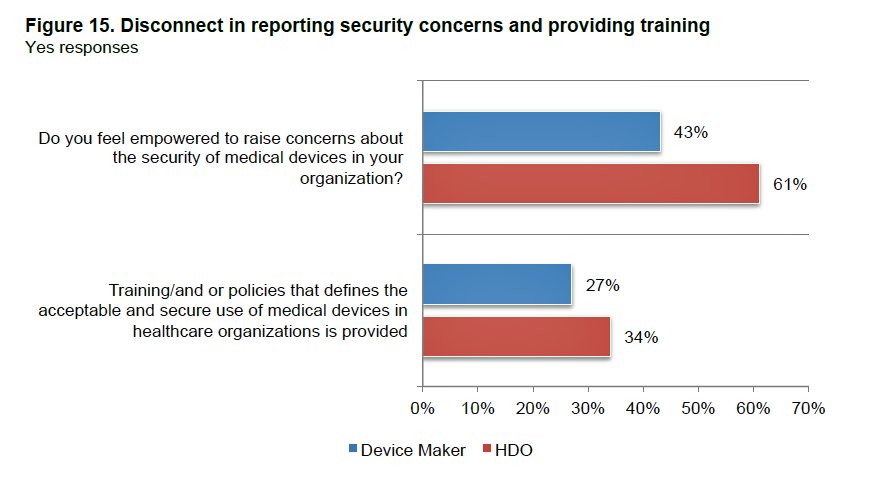
Among the starkest and sobering findings in this study is the one illustrated by the third chart: that only 41% of device makers feel empowered to raise concerns about the security of medical devices in their companies. Most, but not nearly the vast majority, of healthcare providers do.
The accountability for the security of medical devices is unclear in many organizations. For one-third of both makers and providers, no one person is primarily responsible for medical device security, Ponemon learned. In 41% of provider organizations, the user of the medical device is responsible for security — say a surgeon or a doctor.
Health Populi’s Hot Points: In light of the growing risk for medical device security, the ECRI Institute published recommendations for protecting these systems as the Ponemon Institute/Synopsys report went to print this month. The recent WannaCry ransomware attack disrupted hospitals in the UK’s National Health Service systems, along with many organizations outside of healthcare. For the NHS, impacts included appointment cancellations, postponement of surgeries, and emergency vehicle disruptions.
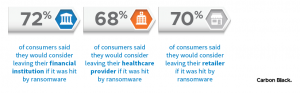 Carbon Black, a security consultancy, conducted a consumer survey following the WannaCry incident, summarizing the poll results in their report, Ransom-Aware. Over half of consumers first learned about ransomware due to the WannaCry event. Among the 5,000 U.S. consumers analyzed by Carbon Black, 7 in 10 people said they’d consider leaving their healthcare provider if hit by ransomware. This survey also found that far more consumers (42%) said their most important information was financial data, and only 5% of consumers said the most important data was their medical records — the same percent saying phone data like messages and contacts was most important.
Carbon Black, a security consultancy, conducted a consumer survey following the WannaCry incident, summarizing the poll results in their report, Ransom-Aware. Over half of consumers first learned about ransomware due to the WannaCry event. Among the 5,000 U.S. consumers analyzed by Carbon Black, 7 in 10 people said they’d consider leaving their healthcare provider if hit by ransomware. This survey also found that far more consumers (42%) said their most important information was financial data, and only 5% of consumers said the most important data was their medical records — the same percent saying phone data like messages and contacts was most important.
As healthcare providers and patients adopt more digital technologies to wear and live with at home and on-the-go, via wearables and robots and implanted sensors, these risks will hit closer to home. And home is where many of us envision as the new-and-improved medical home. But there’s no “improved” here without baking in sober, sound, and holistically-planned security for patients and providers. Without a sound risk management approach to security in medical devices, the promise of the Internet of Healthy Things for peoples’ well-being will be at risk itself.




 I'm in amazing company here with other #digitalhealth innovators, thinkers and doers. Thank you to Cristian Cortez Fernandez and Zallud for this recognition; I'm grateful.
I'm in amazing company here with other #digitalhealth innovators, thinkers and doers. Thank you to Cristian Cortez Fernandez and Zallud for this recognition; I'm grateful. Jane was named as a member of the AHIP 2024 Advisory Board, joining some valued colleagues to prepare for the challenges and opportunities facing health plans, systems, and other industry stakeholders.
Jane was named as a member of the AHIP 2024 Advisory Board, joining some valued colleagues to prepare for the challenges and opportunities facing health plans, systems, and other industry stakeholders.  Join Jane at AHIP's annual meeting in Las Vegas: I'll be speaking, moderating a panel, and providing thought leadership on health consumers and bolstering equity, empowerment, and self-care.
Join Jane at AHIP's annual meeting in Las Vegas: I'll be speaking, moderating a panel, and providing thought leadership on health consumers and bolstering equity, empowerment, and self-care.